theory behind authentication
Quick primer: how does basic authentication using tokens work? Once the user logs in successfully, he receives a token by which he can be identified. This token is saved in the session, in our case a secure cookie. Once the user switches the page, this cookie is read by the server, which allows the server to authenticate the user since it now knows who he is, since this cookie can’t be changed unless you reveal your secret key.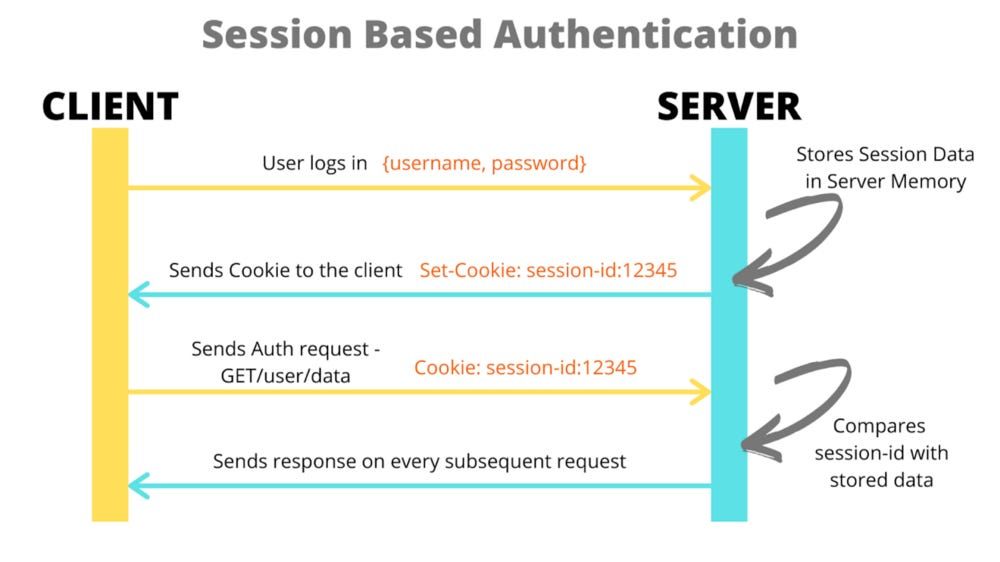 source: https://javascript.plainenglish.io/react-native-cookie-authentication-83ef6e84ba70
source: https://javascript.plainenglish.io/react-native-cookie-authentication-83ef6e84ba70
implementing OAuth
Now the next logical step would be to build a simple email login page and do this manually, but we don’t. Instead we use OAuth: the user logs in with another provider like Google or GitHub with their existing accounts. The provider then generates the token themselves and gives it to us, so we can access information about the user like his email. Why do we do this? Well, originally OAUTH was created for app-developers to perform actions on behalf of a user (learn more in this 5 minute video). However, the main selling point is the user experience: it is much easier to have one Google account which you use to login everywhere instead of creating hundrets of separate accounts. How does this work? First we need to create a new application at an OAuth provider like in our case GitHub and configure a callback adress. This is where the user will be sent once he is done logging in. For GitHub follow this video and usehttp://localhost/** for local development or your domain name
once you have deployed your application.
Open bp_auth.py:
bp_auth.py
.env file.
Now let’s look at the routes managing the authentication. If a user tries to access a route, which he is not authorized to
use, or manually clicks the sign-up button, he will be redirected to “/authenticate”.
bp_auth.py
authorize_redirect function. To it, we pass a callback URL, which
consists of our host, the “/callback” route and a “next” query parameter which displays where the user was planning to
go originally. This callback URL HAS to match the pattern, that we provided in our OAuth application settings, since GitHub
doesn’t want the user to be sent to malicious sites, if the secret keys are compromised.
Once the user has logged in, he is redirected to our “/callback” route. Note, that besides the “next”
query parameter we provided, GitHub also added a “code” one. This is a token which, together with the client secret, we can
exchange for an access token. This access token is “like an API key” and allows us to fetch data about the user like his email.
bp_auth.py
req.py file, you can see the two functions performing these actions.
req.py
add_user function which will save this user to our database. Read the next chapter to
learn how
